7 steps to getting compliant with GDPR or User Guide to the Data Protection Regulation
Just a quick recap: The EU General Data Protection Regulation (GDPR) replaces the Data Protection Directive 95/46/EC and was designed to harmonize data privacy laws across Europe, to protect and empower all EU citizens data privacy, and to reshape the way organizations across the region approach data privacy.
Enforcement date: 25 May 2018
Objectives of GDPR:
- Establish data privacy fundamental right
- Clarify the responsibilities of the parties
- Define baseline for Data Protection
- Elaborate on the data protection principles
- Increase enforcement powers
We won’t describe what GDPR is. There are already plenty of articles about this topic. For example, see a very easy infographic made by the official General Data Protection Regulation office.
After we found a few definitions and made sense of what GDPR is, let’s jump to a step-by-step manual on how to set your company’s GDPR compliance or “What-needs-to-be-done list”.Let`s divide the GDPR manual into 3 parts, Assessment, Evaluation, and Audit. These 3 parts are further divided into 7 steps that can help you make sense out of that regulation.
Note: This is a High-Level Planning to give an overall idea of the work scope. Further investigations and processes must be established. Separate steps may vary depending on the nature of your business. Make sure to advise your business lawyer and internal security officer on the precise action plan.
GDPR Manual:
ASSESSMENT
1. Extra-territorial reach
First of all, there is a big chance that your company falls under GDPR regulations. If your company has an office in the EU, does business with EU citizens or stores any EU citizen PII (Personal Identifiable Information), you need to adapt your business to GDPR to avoid high penalties for your business. If this is the case, please read ahead.
2. Data Audit
Article 35 GDPR: Data protection impact assessment: “… the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data. A single assessment may address a set of similar processing operations that present similar high risks.”
GDPR regulation obliges the companies to make a summary audit of the current systems, databases, and data storage, access level by users, and purpose of data storage. Once you have sketched your entire environment, databases, and location of PII in your internal databases, justified the purpose of each PII storage, and listed the users who have an access to that PII, you can proceed to the next step: Risk Assessment.
3. Risk Assessment
Based on your data audit, it’s important to make a risk assessment paper identifying all the weak spots in your current system where the data breach can happen. Based on the risk assessment audit you need to identify the points of improvement. What can be done better? Where do you think you are lacking either legal or digital security? Who has access to the PII and why? Restrict employees who don’t need to have access there and reestablish processes in the organization with the regard to the risk assessment and GDPR.
4. Data Subject rights
Data Subject or a person whose PII is stored on your organization has a right to request, delete and restrict your organization from gathering further information on him or her. You should establish new processes with regard to these rights.
Don’t forget: Do you store data on EU citizens under 16 years old? For example, the names and age of your employees’ children? If yes, it needs to be tackled in a different way too.
EVALUATION
5. Data Security
Article 25 GDPR: “… The controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organizational measures, such as pseudonymization, which are designed to implement data-protection principles, such as data minimization, in an effective way and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects.”
The main point of GDPR is data security to protect PII stored in the company. Based on your Data Audit and Risk Assessment, it is time to define what data security measures are vital for your organization to prevent major data leakages and unauthorized usage.
Oracle Advanced Security addresses such challenges through preventive controls that are transparent to most applications and with very minimal impact on performance and ongoing IT operations. Oracle provides an easy-to-implement suite of preventive controls that helps organizations implement the key preventive techniques mandated by GDPR including encryption, pseudonymization, anonymization, privileged user control, fine-grained access control, and data hiding.
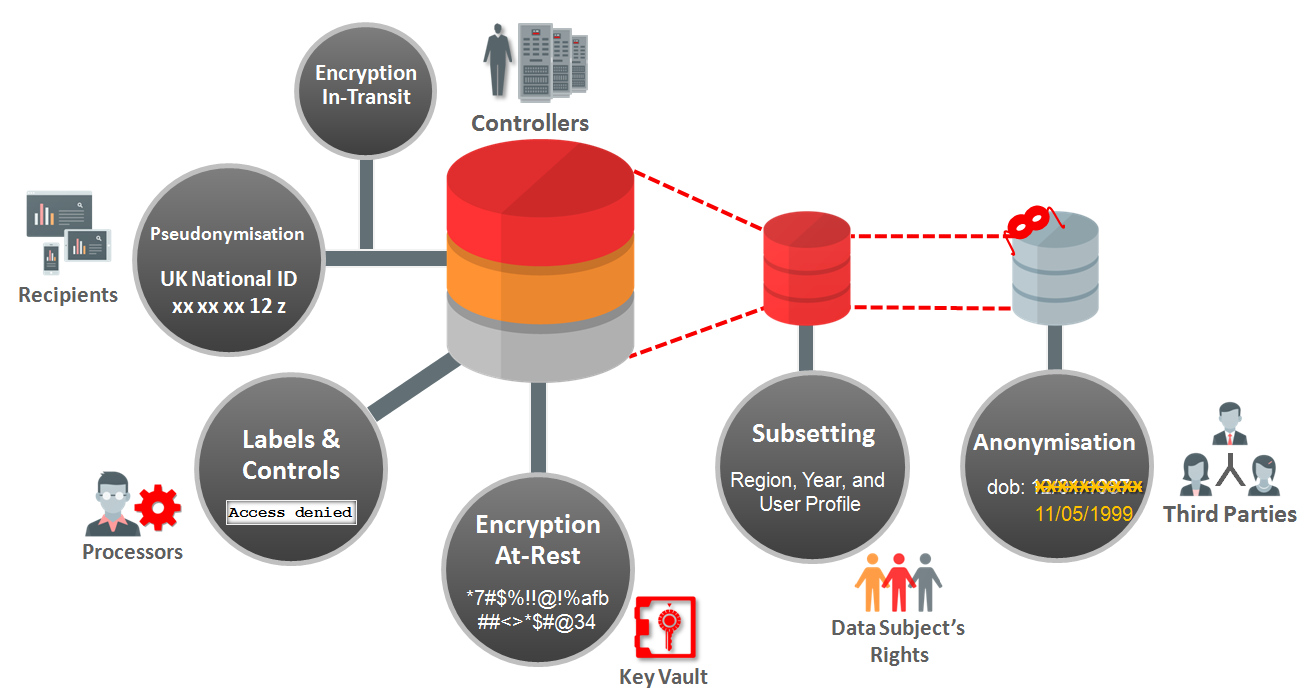
Oracle Database Vault
Traditionally it has been difficult to restrict privileged users (e.g., DBAs) from accessing the Personal Data. Such restrictions might affect day-to-day operations, such as patching and maintenance. Oracle Database Vault embeds privileged user access control within the Oracle Database to limit access to Personal Data by privileged users while allowing the DBAs to perform their regular operational activities such as patching, import, export, and backup without accessing the Personal Data.
Oracle Database Vault is used to define the realm of Personal Data that needs to be protected not just from the privileged users, but also through the use of database commands. It controls the mechanisms and the factors that can be used by the controllers, processors, and third parties (authorized users) to access Personal Data.
AUDIT
Article 30 GDPR: “Each controller and, where applicable, the controller’s representative, shall maintain a record of processing activities under its responsibility. “
6. Data Protection Officer (DPO)
Some organizations will be obliged to assign a DPO role to one of the employees. In case you are a public entity, you process sensitive information (health, crime records etc.) or your organization profits from data processing, then you should think of who is the best DPO candidate, as you are subject to Article 37 GDPR.
7. Data Breach
Article 33 “In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority …”
Establish processed with regards to Article 33, make sure you know the contact information of your GDPR authority in the country of your company`s HQ.
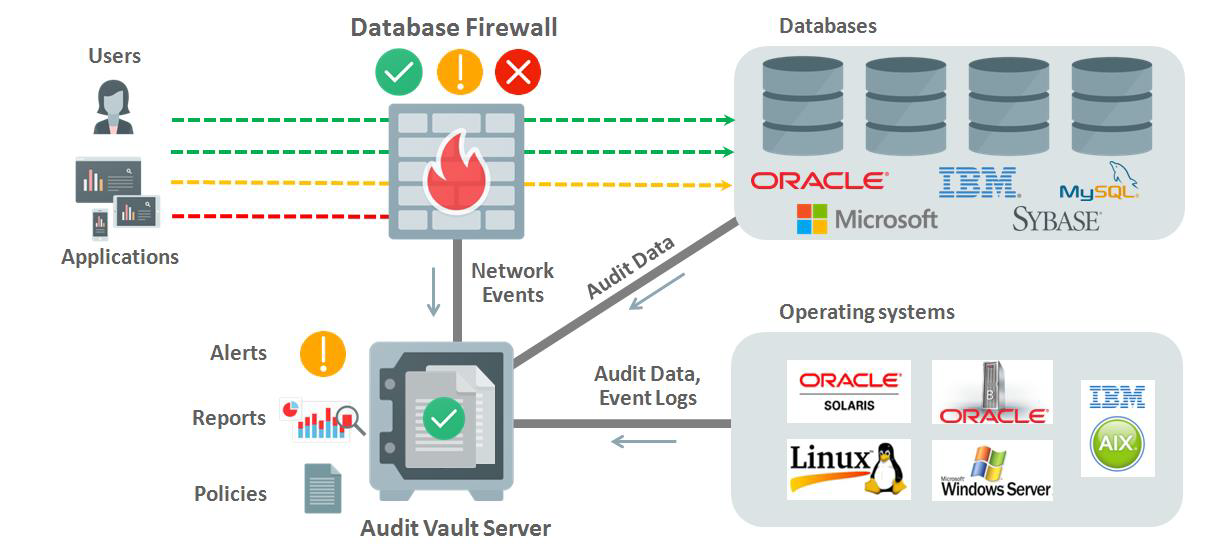
Oracle Database Audit
It provides a next-generation data-centric audit and protection (DCAP) platform that provides comprehensive and flexible monitoring through consolidation of audit data from Oracle and non-Oracle databases, operating systems, file systems, and application-specific audit data.
As a good prevention method, you could establish the alerts and records with Oracle Database Vault to centrally store and monitor all records and activities.
At Quistor we are pleased to advise you on the best technological solutions that can facilitate compliance with these regulations.

